“Email Authentication” is a technique that ensures a message’s recipient actually came from the claimed source. The goal is to protect recipients from phishing and spoofing, which can erode their trust in email. Sending authenticated email does not mean the email is good or wanted; it only means the sender’s reputation can be reliably established and used in email acceptance and placement decisions.
SPF and DomainKeys Identified Mail are two popular email authentication methods (DKIM). We’ll explain SPF in this blog post.
- Authentication “Path-Based”
- SPF Policy Declaration
- What’s SPF Authentication?
- HELO or MAIL FROM?
- SPF Isn’t Perfect
- Conclusion
Authentication “Path-Based”
SPF is a path-based authentication system because it’s tied to the message’s origin-to-destination path. The receiving server determines whether a sending server is authorized to send a message based on the domain’s SPF policy. It’s based solely on the message’s source, not its content.
SPF Policy Declaration
A domain’s SPF policy record is a DNS TXT record with one or more “mechanisms”
- v=spf1 – Required first token for TXT SPF record (a domain can have multiple TXT records)
- ipv4, ipv6 – this is use for specifying IP addresses and networks that can send domain mail.
- a – The sending IP is allowed if the sending domain’s DNS “A” record resolves to it.
- mx – If the sender IP is one of the domain’s MX records, it’s allowed.
- all – Last token, always modified
What is SPF Authentication?
SPF is an email authentication protocol that verifies that the sender’s domain name in the From: field matches the sender’s domain name. The sending MTA will use DNS to query a preconfigured list of SPF servers to determine whether or not the sending IP is permitted to send email for the domain. There may be inconsistencies in how SPF records are configured, which is essential to understanding why emails can fail SPF verification and what you can do to prevent problems with your own email marketing campaigns.
HELO or MAIL FROM?
SPF requires recipient sites to validate the MAIL FROM domain and RECOMMENDS examining the HELO hostname. In practice, only the MAIL FROM domain is checked, unless the MAIL FROM address is the NULL sender (i.e., “>”). In that instance, only the HELO hostname is available.
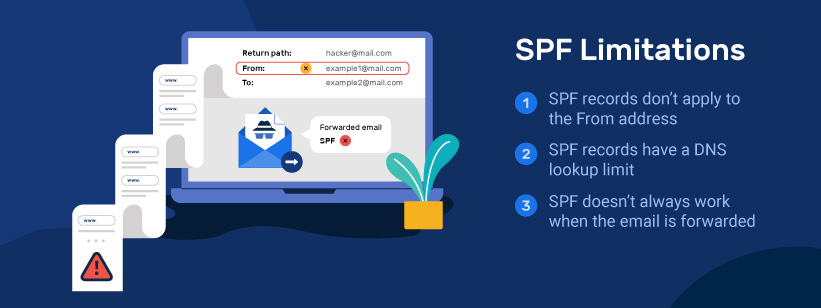
SPF Isn’t Perfect
SPF sounds like a simple approach to validate email, but it’s prone to false negatives. These failures might be frequent.
Two common situations when legitimate mail fails SPF certification and appears fraudulent:
- Automated forwarding, where [email protected] automatically forwards messages to [email protected]
- Mailing lists, where mail submitted to [email protected] is “exploded”
If the Return-Path remains unaltered, the mail may fail SPF checks (depending on the ‘all’ modifier). It reaches at its final destination from an intermediary server, not the original one, and that intermediate server isn’t in the domain’s SPF record. “Sender Rewriting Scheme” or “SRS” can reduce this risk, although it’s not universal.
